QBot Trojan upgraded to a ransomware, abusing Win10 Writing Board executable, hijacking DLLs to infect devices.
Tech media outlet BleepingComputer reports that security experts and Cryptolaemus member ProxyLife have discovered a new QBot phishing campaign that abuses the writing pad executable write.exe on Win10 systems to spread via a DLL hijacking vulnerability.
QBot, also known as Qakbot, is a Windows malware that originally appeared as a banking Trojan and then evolved into a malware dropper.
Security experts have now confirmed that ransomware groups such as Black Basta, Egregor and Prolock are using the malware to launch ransom attacks on multiple corporate networks.
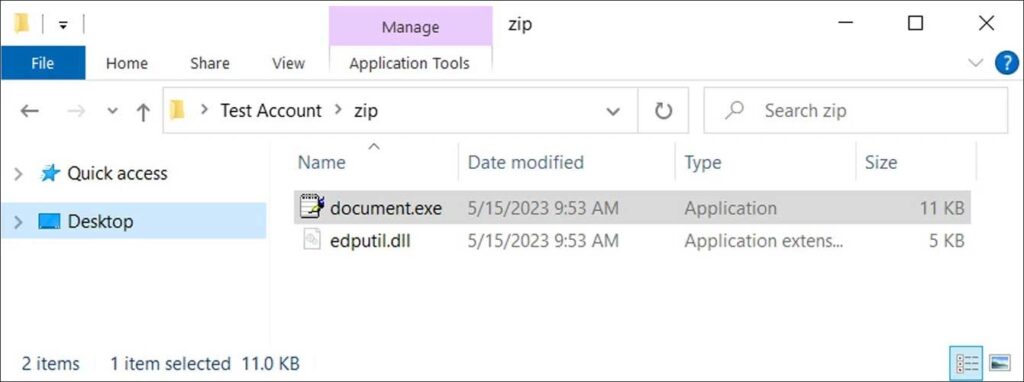
When a victim clicks on the link, a randomly named ZIP archive is downloaded from a remote host. The file contains document.exe and a DLL file named edputil.dll (used for DLL hijacking).

Checking the document.exe property, you can see that it is a renamed version of the legal writing pad file Write.exe.
When document.exe starts, it automatically tries to load a legal DLL file named edputil.dll, which is usually located in the C:\Windows\System32 folder.
When the executable tries to load edputil.dll, the problematic edputil.dll file in the same file path is loaded first.